How to Use Set-ExecutionPolicy in Powershell
By default, PowerShell restricts script execution to protect users from running potentially harmful code. This default behavior is controlled by execution policies. To adjust what scripts are allowed to run, you use the Set-ExecutionPolicy cmdlet.
Whether you're configuring a machine for local script testing or deploying scripts across an organization, knowing how to control execution policies is essential to managing PowerShell securely and effectively.
What is the Set-ExecutionPolicy Cmdlet?
The Set-ExecutionPolicy cmdlet lets you modify the execution policy - a security setting that defines which scripts PowerShell will run. It's not a true security boundary, but rather a safety feature that helps prevent accidental or unapproved script execution.
This cmdlet is mainly used to lower or raise restrictions on script execution, depending on your scenario. It's often used in development environments or during configuration automation, and must be handled carefully, especially when used with broader scopes like LocalMachine.
Syntax Block with Parameters
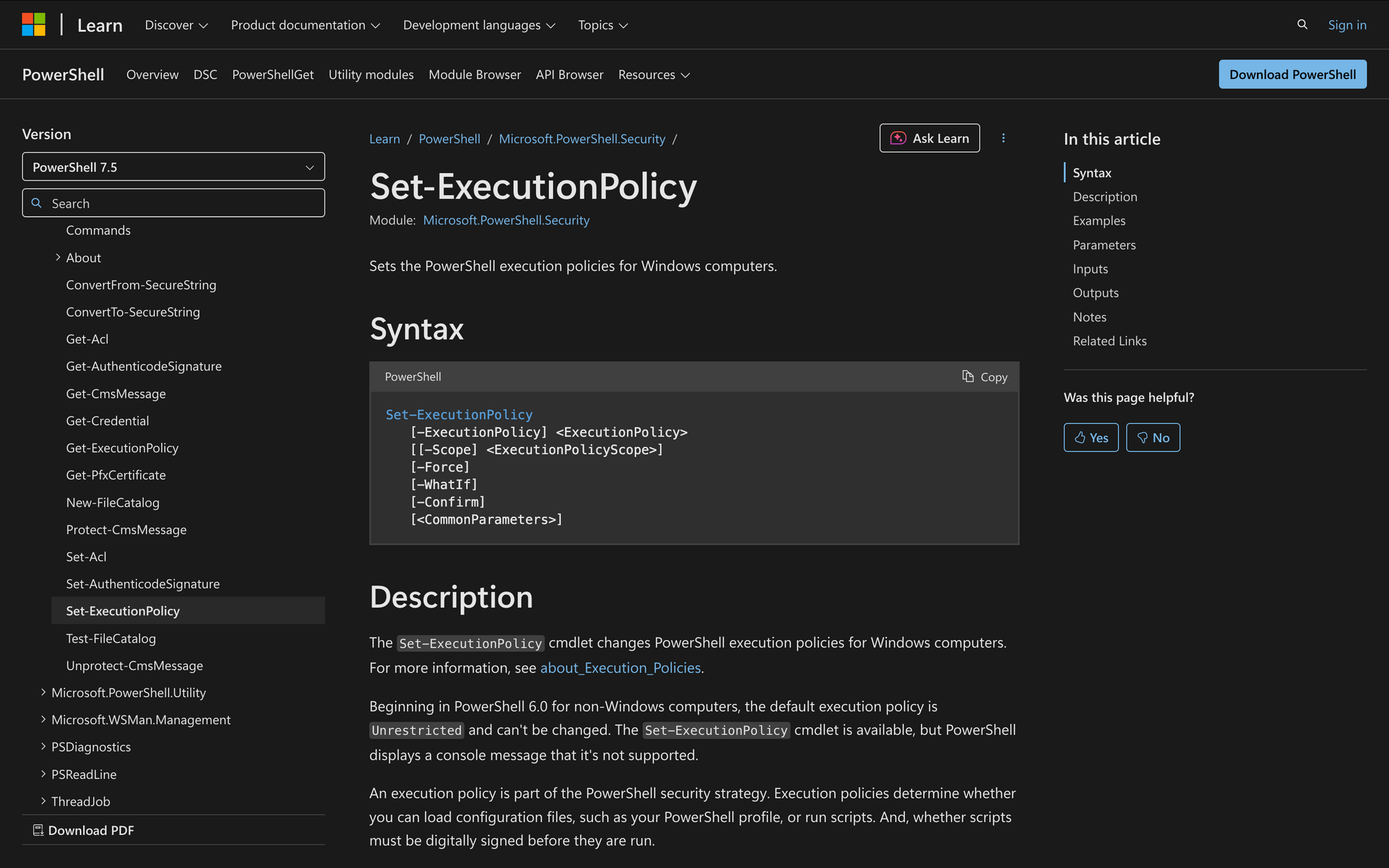
Set-ExecutionPolicy
[-ExecutionPolicy] <ExecutionPolicy>
[[-Scope] <ExecutionPolicyScope>]
[-Force]
[-WhatIf]
[-Confirm]
[<CommonParameters>]
Parameters
- -ExecutionPolicy: Required. Specifies the policy you want to apply. Acceptable values include Restricted, AllSigned, RemoteSigned, Unrestricted, Bypass, and Undefined.
- -Scope: Limits the change to a specific scope like Process, CurrentUser, or LocalMachine. Defaults to LocalMachine if omitted.
- -Force: Suppresses the confirmation prompt.
- -WhatIf: Shows what would happen if the cmdlet runs, without making changes.
- -Confirm: Prompts for confirmation before making changes.
- <CommonParameters>: Includes standard PowerShell parameters like Verbose, ErrorAction, etc.
Practical Uses
Here are three common, real-world scenarios where you would need the Set-ExecutionPolicy cmdlet:
1. Enabling Local Script Development
A developer wants to run unsigned PowerShell scripts they're writing on their own machine. By default, the Restricted policy blocks all scripts. They use Set-ExecutionPolicy to change the current user scope to RemoteSigned, allowing local scripts while still blocking unsigned remote scripts.
2. Running Automated Deployment Scripts Across Machines
An IT admin pushes scripts to multiple machines using Invoke-Command. Some of these machines have strict execution policy settings that block script execution. To ensure scripts run as intended, the admin sets the execution policy to Bypass within the process scope, avoiding permanent policy changes.
3. Fixing Script Load Failures in CI/CD Pipelines
A CI runner fails to execute a script because the execution policy is set to Restricted. The pipeline includes a task to run Set-ExecutionPolicy -ExecutionPolicy Bypass -Scope Process as a temporary override, enabling the unsigned script to run without altering the system-wide configuration.
In each case, controlling the effective execution policy at the appropriate scope prevents unnecessary friction while preserving control. Knowing when to apply a separate execution policy per context is key to balancing security and usability.
Prerequisites
Before using Set-ExecutionPolicy, make sure you meet these requirements:
- Administrator rights are required to set the policy at the LocalMachine or MachinePolicy scope.
- PowerShell version 2.0 or higher is required (included in most modern Windows systems).
- You must run PowerShell as Administrator to change the policy for machine-wide or all-users scopes.
- For systems managed by Group Policy, execution policies set by MachinePolicy or UserPolicy will override local settings. These settings can’t be changed using Set-ExecutionPolicy.
- Know the acceptable execution policy values: Restricted, AllSigned, RemoteSigned, Unrestricted, Bypass, Undefined.
- Understand how the PSExecutionPolicyPreference environment variable can influence behavior in some automation setups.
- Be aware that Unsigned scripts from the internet or downloaded files may still be blocked unless unblocked manually (e.g., using Unblock-File cmdlet).
These prerequisites are especially important if you're scripting for environments like Windows Server or when dealing with multiple users, where aGroup Policy may enforce a strict default execution policy.
How to Use Set-ExecutionPolicy: 7 Examples
The Set-ExecutionPolicy cmdlet changes the PowerShell execution policy settings to determine which scripts are allowed to run on your system. Below are practical, step-by-step tasks showing how to use it in different scopes and contexts.
1. View Your Current Execution Policy
Before making changes, check the current policy.
Get-ExecutionPolicy
To see the effective execution policy for all scopes:
Get-ExecutionPolicy -List
This shows which policy is currently in effect based on precedence: MachinePolicy > UserPolicy > Process > CurrentUser > LocalMachine.
2. Change Execution Policy for LocalMachine (Default Scope)
This sets the policy for all users on the system. You must run PowerShell as Administrator.
Set-ExecutionPolicy RemoteSigned
This command sets the RemoteSigned policy for the LocalMachine scope, which is the Set-ExecutionPolicy cmdlet's default scope. It allows scripts to run if they are either locally created or digitally signed.
3. Set Execution Policy for CurrentUser Only
If you don’t want to affect other users, use the CurrentUser scope.
Set-ExecutionPolicy RemoteSigned -Scope CurrentUser
This is useful for individual developers or users needing looser restrictions without impacting system-wide configuration.
4. Temporarily Bypass Execution Policy for One Session
For automation or testing, use the Process scope. This lasts only for the duration of the session.
Set-ExecutionPolicy Bypass -Scope Process
This does not persist after the session ends, making it ideal for CI/CD pipelines or scripting tasks that shouldn't alter the system's configuration.
5. Use With Force to Skip Confirmation Prompts
To automate changes, use the -Force parameter to suppress the confirmation dialog.
Set-ExecutionPolicy Unrestricted -Scope CurrentUser -Force
This is helpful when scripting or remotely applying settings via the Invoke-Command cmdlet.
6. Revert Execution Policy to Undefined
To remove the policy for a given scope, use Undefined. PowerShell will then fall back to a higher-precedence policy, such as one set via Group Policy.
Set-ExecutionPolicy Undefined -Scope CurrentUser
If all scopes are set to Undefined, the effective policy defaults to Restricted, which blocks all scripts.
7. Apply Execution Policy Changes Across Multiple Machines
To configure remote systems, you might combine Set-ExecutionPolicy with Invoke-Command.
Invoke-Command -ComputerName Server01 -ScriptBlock { Set-ExecutionPolicy RemoteSigned -Scope LocalMachine -Force }
Make sure PowerShell remoting is enabled and you're running with administrative privileges. Be cautious: applying RemoteSigned or Unrestricted policies remotely can introduce security risks if not controlled carefully.
The Set-ExecutionPolicy cmdlet is a critical part of PowerShell’s security strategy, allowing you to define what types of scripts are permitted to run across different scopes.Knowing how to check, change, and reset your execution policy gives you tight control over your scripting environment - especially when dealing with unsigned scripts, CI pipelines, or secured enterprise networks.

