Using Enable-PSRemoting in Powershell
Do you know how to use PowerShell remoting? If not, we’ve got you covered. PowerShell remoting is a powerful feature that allows administrators to execute commands on remote systems.
The Enable-PSRemoting cmdlet is the first step in configuring your system for this capability. In this article, we’ll explore how to enable and manage PowerShell remoting effectively, unlocking a range of possibilities for remote administration.
What is Enable-PSRemoting in PowerShell?
Enable-PSRemoting is a PowerShell command that prepares a computer to receive remote commands through PowerShell's remoting feature, which relies on WS-Management technology. By running this command, it activates listeners, configures necessary firewall rules, and starts the WinRM (Windows Remote Management) service, enabling other computers to connect and execute commands remotely.
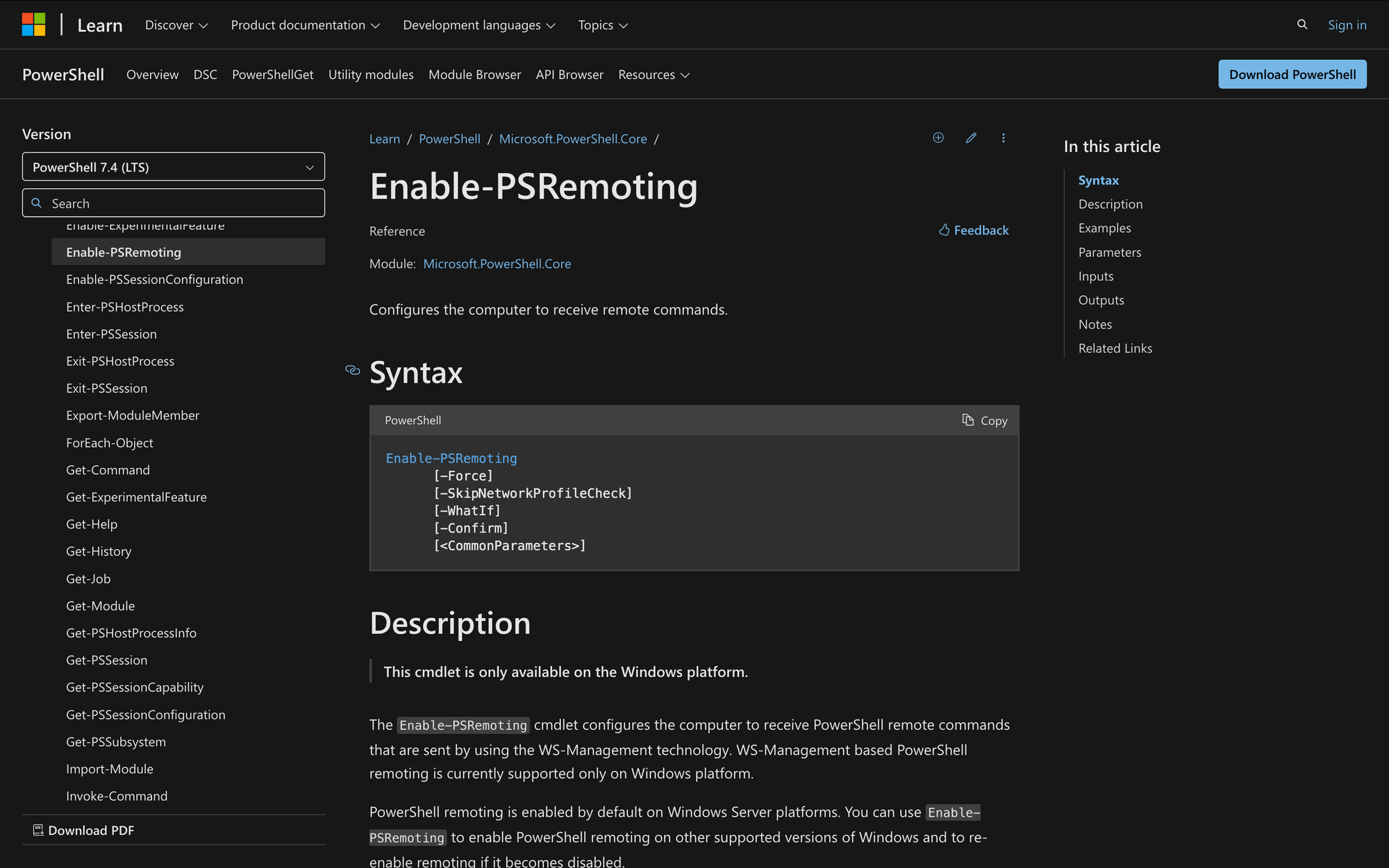
Here’s the syntax of Enable-PSRemoting and a brief explanation of each parameter:
- -Force: Runs the command without any confirmation prompts, useful for scripting.
- -SkipNetworkProfileCheck: Allows remoting on public networks by adjusting firewall rules for the local subnet.
- -WhatIf: Shows what would happen if the command runs without actually executing it.
- -Confirm: Prompts for confirmation before running, adding a safety check for the command.
- <CommonParameters>: Standard PowerShell parameters, like -Verbose and -ErrorAction, that control command behavior and output.
What Can You Use Enable-PSRemoting For in PowerShell?
Let’s now take a quick look at 3 use cases for Enable-PSRemoting:
- Remote System Management: Admins can manage multiple computers across a network by remotely executing commands (you might need the remote server’s credentials first), installing software, updating configurations and performing system diagnostics without physically accessing each machine.
- Automated Deployment and Configuration: Enable-PSRemoting lets you run scripts across various machines to automate the setup of new servers, configure settings, or apply security patches in bulk, saving time and ensuring consistency.
- Monitoring and Troubleshooting: The command also allows remotely running diagnostic commands and gathering system data (like CPU usage, memory status, or event logs) to troubleshoot and monitor system health across multiple systems in real-time.
Prerequisites to Run the Enable-PSRemoting Windows PowerShell Command
Before using this cmdlet, make sure to comply with the following prerequisites:
- Run as Administrator: PowerShell needs to be launched with administrative rights since enabling remoting modifies system settings, starts services, and creates firewall exceptions. Without admin privileges, the cmdlet won’t execute successfully.
- Windows Platform Requirement: Enable-PSRemoting is built specifically for Windows, as it leverages WS-Management and the WinRM (Windows Remote Management) protocol, which aren’t natively supported on Linux or macOS. For cross-platform remoting, other configurations like SSH-based remoting are required.
- WinRM Service Active: Since PowerShell remoting depends on WinRM to handle remote command execution, WinRM must be installed and running. The Enable-PSRemoting cmdlet starts WinRM automatically if it’s not already active, but it must be present on the system.
- Firewall Rules for Network Access: To connect remotely, appropriate firewall settings must be in place to allow traffic over WinRM ports (default HTTP port 5985 and HTTPS port 5986). Enable-PSRemoting configures these exceptions for private and domain networks, but additional steps may be needed on public or highly restricted networks.
5 Steps to Effectively Use Enable-PSRemoting
Now that you know what you need to use this command, it's time to execute it!
Step 1: Open PowerShell as Administrator
To configure PowerShell remoting, launch PowerShell with administrative privileges. This step is crucial because enabling remoting involves modifying system settings that require elevated permissions.
To do this, right-click on the Start button in the Windows taskbar and select Windows PowerShell (Admin) or Terminal (Admin) from the context menu.
Running PowerShell as an administrator ensures that you have the necessary rights to execute the remoting setup commands without encountering permission errors.
Step 2: Enable PowerShell Remoting on Your Machine (Use the Command!)
Once you have PowerShell open with administrative rights, you can proceed to enable remoting. This is done using the Enable-PSRemoting cmdlet, which configures your computer to accept remote commands:
After you run this, the cmdlet performs the following actions:
- Starts the WinRM Service: This service is essential for PowerShell remoting, as it allows the computer to communicate over the network using the WS-Management protocol.
- Sets WinRM to Automatic: Ensures that the WinRM service starts automatically every time the computer boots up.
- Creates a Listener: It establishes a listener on all IP addresses to accept remote commands.
- Enables Firewall Exceptions: Configures the Windows Firewall to allow WS-Management traffic, ensuring that remote connections are not blocked.
After running this command, you should see a confirmation message indicating that PowerShell remoting has been successfully enabled.
Step 3: Skip Network Profile Checks for Public Networks (Optional)
On a public network, enable remoting by accounting for the security settings that typically prevent this action. Using the -SkipNetworkProfileCheck parameter lets you bypass the restriction against enabling remoting in public networks, according to Microsoft.
In this case, run the command like this:
While this command is useful, be aware that enabling remoting on a public network can expose your computer to security risks. Ensure that your firewall and security settings are appropriately configured to protect your machine, and only follow this step if you really need to.
Step 4: Check Configured Remoting Endpoints
After enabling remoting, it’s important to verify that the appropriate remoting endpoints have been created. Remoting endpoints define how PowerShell sessions are handled and which versions of PowerShell can be used remotely.
To list the endpoints, use this command:
The command outputs the names and configurations of the remoting endpoints, showing you the available PowerShell versions for remote sessions. So, for instance, you might see something like this:
This confirms that remoting is enabled and indicates which users can access the session.
Step 5: Test the Remote Connection
To ensure that remoting is working correctly, you should test it by creating a remote session. This can be done on the local machine (loopback) or to another computer on your network.
To create a remote session, run this command (example):
Once the session is created, you can run a command within that session. For example, to check the version of PowerShell, do this:
The command should return the version of PowerShell currently running in the remote session. This confirms that your remoting setup is working as intended.
If everything is set up correctly, you should see the PowerShell version output without any errors, indicating successful remote communication.
As you can see, enabling PowerShell remoting with Enable-PSRemoting streamlines remote management, allowing you to execute commands on multiple systems effortlessly. With this feature, you can enhance your administrative tasks and improve efficiency right away.

